On Ubuntu and Debian hosts, the single user mode, also referred as the rescue mode, is used to perform critical operations.
The single-user mode can be used to reset the root password or to perform file systems checks and repairs if your system is unable to mount them.
In this tutorial, we are going to see how you can boot on single user mode on Debian and Ubuntu hosts and how to reset the root password.
We are also configure our target units (rescue and emergency) to prompt for a password on single-user mode boot.
Note: in order to boot into rescue or emergency targets, you are need physical access to the machine to interrupt the default GRUB boot process.
Rescue & Emergency Targets on Debian
On recent Debian distributions, systemd is responsible for booting your Linux host using a default target.
If you want to check the default target run by systemd, you can run the following command
$ systemctl get-default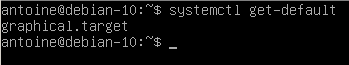
As you can see, my system is set to boot on graphical target by default.
As I don’t own any desktop environment like GNOME or KDE, it is going to boot in a simple shell.
However, the graphical target is not the only target available on Linux, you can boot in the following modes:
- poweroff : used to shutdown your host and power off the system;
- rescue : a mode used to boot your system with a rescue shell;
- emergency : similar to the rescue mode except that no services are launched and no filesystems are mounted;
- multi-user : the default mode on Linux systemd systems, used to boot your host in a non-graphical system (without a desktop environment);
- graphical : includes the multi-user target and a graphical environment such a KDE or GNOME for example;
- reboot : shutdowns the system and reboot it immediately
As their names reflect it, those modes are used in order to perform maintenance operations on a Linux system, but they need to be done securely to avoid any security leaks.
In this article, we are going to focus on the rescue and emergency modes and see how we can securely on them.
We are also going to see how booting in single user mode can be used to change the root password or to perform simple filesystems checks.
Configuring the Root Account on Debian
By default, when entering single user mode, you are going to be given a root prompt with complete privileges.
As a consequence, in order to boot in single-user mode (or rescue mode), your root account needs to be unlocked and it needs to have a password.
Checking Root Account Lock Status
On Ubuntu, root accounts are disabled by default as a security measure, and you can choose to have it disabled on Debian 10 also (if you don’t specify a root password when installing Debian)
In order to check if your root account is locked, run the following command
$ sudo -s
$ cat /etc/shadow | grep root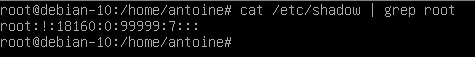
As you can see, there is an exclamation mark on the space reserved for the password : it means that the root is locked.
Setting a Root Account Password
In order to set a password for the root account, run the following command
$ sudo passwd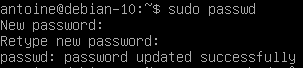
If you go back to check the content of your shadow file, you should now see that the content has been modified and that no exclamation mark are presented.
Awesome, now we can start booting into single user mode from the GRUB bootloader screen.
Booting in Rescue Mode from GRUB
In order to boot into single user mode, or rescue mode, you are going to interrupt the default boot process when starting your machine.
Reset your machine and interrupt the boot process by pressing a key arrow in the GNU GRUB menu.
If you are running a Debian based distribution, this is what you should see on your screen
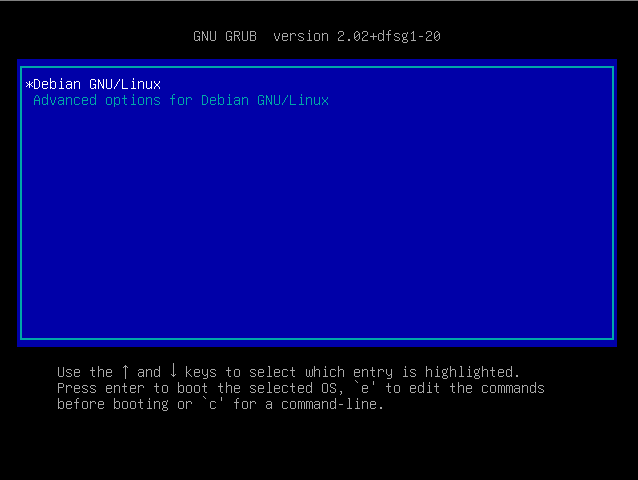
As described in the bottom description panel, press ‘e’ in order to edit the boot commands
You should now see the following window on your screen
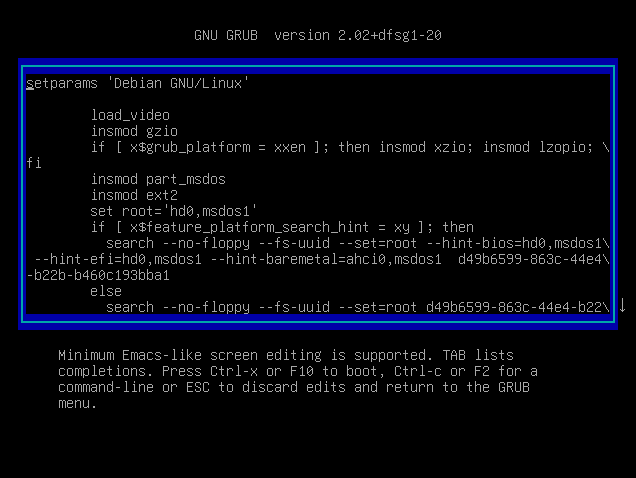
Using the directional arrows, navigate to the Linux kernel booting line and put the following string at the end of the line.
systemd.unit=rescue.targetYou can also simply type “1”, it is equivalent to booting in single user mode on Debian.
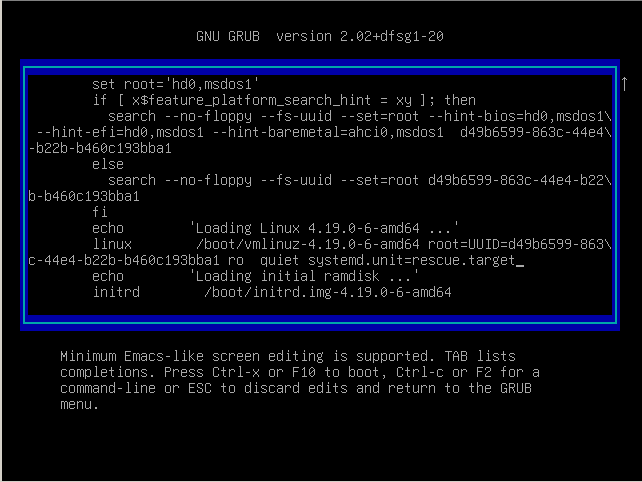
As described below the boot script, press F10 to boot into rescue target.
Your Linux Kernel will be loaded and your initial virtual filesystem will be loaded.
Before having the access, you will be prompt with the root password that you just changed before.
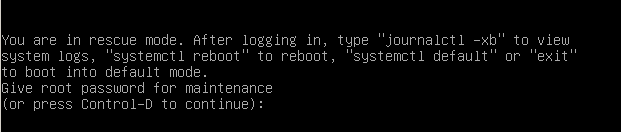
Type the password you defined before, and you should now have a root shell directly into your host.
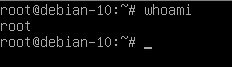
Awesome! Now that you have a root shell into the host, you can start by changing the root password or by checking your filesystems.
Security Recommendations for Single User Mode
When it comes to the single user mode, or the rescue target, it is important that this mode is password-protected on your system.
As you can see, it is the case by default on Debian 10, but you have to make sure on other distributions that it is the case.
If any intruder has physical access to your machine, in a data-center for example, it could be as easy as rebooting the machine, interrupting the boot process and launching a non-protected single user mode.
From there, every file can be deleted, copied or transferred to a non secure server.
Malicious programs can also be installed to track the host activity and to steal personal information.
Sulogin login shell
Luckily for you, standard Debian distributions are configured to ask for the root password when booting in single user mode.
It can be seen by inspecting the rescue and emergency services on your host (located at /usr/lib/systemd/system)
$ cat /usr/lib/systemd/system/rescue.service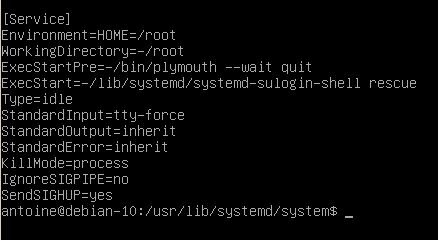
By default, when starting, your system is going to launch the systemd-sulogin-shell in rescue mode, which is safe from unauthorized access.
However, you have to make sure that this file was not altered and that the system is not instructed to launch a simple shell (like /bin/sh for example).
This would result in having an unsafe single user mode, essentially having a major security breach if anyone has physical access to the machine.
Conclusion
In this tutorial, you learnt about the single user mode on Debian-based distributions and how it is related to the rescue and emergency targets on Linux.
You learnt that this mode needs to be password protected as it offers a root shell for users who were to log into it.
You also had a look at how you can instruct the GRUB to boot into this mode, and how it can be used to perform maintenance operations on your system.
If you are curious about Linux system administration, we have a complete section dedicated to it on the website.

Also, make sure to read our most recent post about access control lists on Linux as they define another layer of security on Linux filesystems.


1 comment
[…] you are not sure how you can boot a Debian host in single user mode, you can read this tutorial that we wrote on the […]